Crunch: The All-in-One Wordlist Generator
Published on: September 13, 2025 |
Author: Bibek Singh
⚠️ Legal Warning: Unauthorized use of crunch or similar tools to attack systems without permission is illegal and unethical. Always ensure you have proper authorization before conducting any security testing. The misuse of these tools can result in severe legal consequences.
Introduction to Wordlist Generation in Cybersecurity
In the world of cybersecurity, penetration testing, and password cracking, having the right wordlist can make all the difference between a successful operation and a failed attempt. This is where crunch comes into play - a powerful wordlist generator that has become an essential tool in every security professional's toolkit and ethical hacker's arsenal.
Whether you're testing password strength, performing brute-force attacks (ethically, of course!), generating data for testing applications, or conducting security assessments, crunch provides a flexible and efficient way to create custom wordlists tailored to your specific needs. This comprehensive guide will cover everything you need to know about this powerful Kali Linux tool.
What is Crunch? Understanding the Basics
Crunch is a command-line utility available in Linux that generates wordlists based on criteria you specify. It creates all possible permutations and combinations of characters, making it incredibly useful for:
- Password cracking and password recovery
- Network penetration testing and vulnerability assessment
- Testing application security and authentication mechanisms
- Generating test data for database applications
- Creating sample inputs for software testing
- Wireless network auditing (WPA/WPA2 cracking)
- Dictionary attack simulations for defense testing
Installing Crunch on Various Linux Distributions
Most penetration testing distributions like Kali Linux, Parrot OS, and BlackArch come with crunch pre-installed. If you need to install it on other systems:
On Debian/Ubuntu-based systems:
sudo apt update
sudo apt install crunch
On Fedora/RHEL-based systems:
git clone https://github.com/crunchsec/crunch.git
cd crunch
make
sudo make install
Basic Syntax and Usage of Crunch
The basic syntax of crunch follows this pattern:
crunch [character-set] [options]
Let's break down the components:
- min-length: The minimum length of words to generate
- max-length: The maximum length of words to generate
- character-set: The characters to use (optional - can use predefined sets)
- options: Various flags to control output and behavior
Generating Your First Wordlist: Practical Examples
Let's start with a simple example. To generate all possible 4-character combinations using lowercase letters:
crunch 4 4 abcdefghijklmnopqrstuvwxyz
Or using a predefined character set:
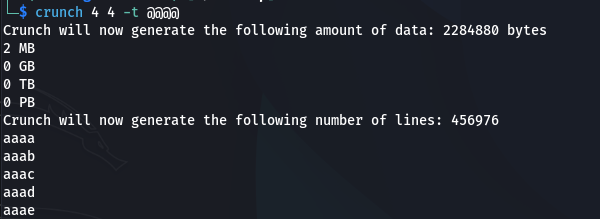
In this example, @ represents lowercase letters. Crunch will generate words from "aaaa" to "zzzz", creating a comprehensive brute-force wordlist.
Understanding Character Sets and Placeholders
Crunch supports both custom character sets and predefined placeholders, making it extremely versatile for different password cracking scenarios.
Predefined Character Sets
- @ - Lowercase alphabetic characters (a-z)
- , - Uppercase alphabetic characters (A-Z)
- % - Numeric characters (0-9)
- ^ - Special characters/symbols (!@#$%^&*()_+-=)
- - - Space character
You can specify exact characters to use:
This will generate all combinations using only 'a', 'b', 'c', '1', '2', and '3'.
Using Multiple Character Sets
You can mix predefined and custom sets for more control:
This generates 5-character words with:
- First character: lowercase letter
- Second character: number
- Third character: symbol
- Fourth and fifth: lowercase letters
Advanced Pattern Generation with Crunch
One of crunch's most powerful features is its pattern matching capability using the -t option, which is particularly useful when you already know or can guess part of a password.
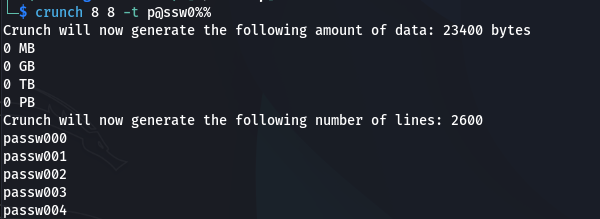
This generates the single word "password". While simple, this demonstrates the pattern capability.
Pattern with Placeholders
Complex Patterns for Common Password Structures
# Common pattern: word + year
crunch 8 8 -t @@@@%%%% -o words_years.txt
# Common pattern: word + number + symbol
crunch 9 9 -t @@@@%^@@ -o complex_pass.txt
# Specific company name with numbers
crunch 10 10 -t COMPANY%%%%
This approach is extremely valuable when you have partial knowledge of password structures, such as knowing that users at a particular company use the company name followed by numbers in their passwords.
Working with Files and Managing Output
By default, crunch outputs to stdout. To save to a file:
crunch 4 4 -o wordlist.txt
If you need to stop and resume generation, use the -s (start) option:
crunch 1 10 -s dg -e hacker -o wordlist.txt
This starts at "dg" and goes until "hacker".
Large wordlists can be split into multiple files to manage size:
crunch 4 4 -b 1mb -o START
This creates files of approximately 1MB each, with names like "START01.txt", "START02.txt", etc.
Crunch can compress output files to save space:
crunch 4 6 -z gzip -o compressed_wordlist.txt.gz
Supported formats: gzip, bzip2, lzma, and 7z.
Performance Considerations and Optimization
Wordlist generation can quickly consume disk space and time. Here's what to expect:
- 4-character lowercase: 456,976 combinations (~2MB)
- 8-character alphanumeric: 218,340,105,584,896 combinations (~2,183 TB)
- 10-character with full charset: 5,720,645,063,660,872,000,000 combinations (5.7 sextillion entries)
As you can see, generating long passwords with full character sets is impractical. Always consider:
- Use realistic length limits based on your testing scenario
- Employ patterns (-t) to reduce combinations when you have partial password knowledge
- Use the -l option when using -t to interpret @,% literally
- Pipe output directly to other tools when possible to avoid storing huge files
- Estimate size first using the -d option before generation
Practical Examples and Use Cases for Security Testing
1. Generating Common Password Patterns
# Common pattern: word + year
crunch 8 8 -t @@@@%%%% -o words_years.txt
# Common pattern: word + number + symbol
crunch 9 9 -t @@@@%^@@ -o complex_pass.txt
2. Creating Wordlists for Specific Services
# For a WiFi penetration test (WPA/WPA2 minimum length is 8)
crunch 8 10 abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 -o wpa_wordlist.txt
3. Generating Targeted Wordlists Based on Known Information
# If you know part of a password (extremely useful in real-world scenarios)
crunch 12 12 -t COMPANYNAME%%%%
# Using known personal information (for ethical password recovery)
crunch 6 8 -t petname%% -o pet_based_words.txt
4. Combining with Other Security Tools
4. Combining with Other Security Tools
# Directly to John the Ripper for password cracking
crunch 6 8 | john --stdin hashes.txt
# Directly to Aircrack-ng for WiFi testing
crunch 8 8 | aircrack-ng -w - capture.cap
# Directly to Hashcat for GPU-accelerated cracking
crunch 6 8 | hashcat -m 0 target_hashes.txt
Integrating Crunch with Other Security Tools
With Hashcat for GPU-Accelerated Cracking
# Generate on the fly for hashcat
crunch 6 8 | hashcat -m 0 target_hashes.txt
# Using rules with crunch output
crunch 5 5 -t @@@@% | hashcat -m 0 -r best64.rule hashes.txt
With Hydra for Network Service Testing
# Create a custom wordlist for HTTP login
crunch 6 10 -t admin%%% | hydra -l admin -P - http-get://target.com/login
Custom Scripts for Automated Testing
Use crunch in your bash scripts for automated security assessments:
#!/bin/bash
# Automated password testing script
TARGET="example.com"
USERNAME="admin"
for length in {6..8}; do
echo "Testing passwords of length $length"
crunch $length $length -t @%%%%% | hydra -l $USERNAME -P - http-form-post://$TARGET/login:username=^USER^&password=^PASS^:invalid
done
Frequently Asked Questions (FAQ)
Q1: What is the maximum password length crunch can generate?
A1: Crunch doesn't have a fixed maximum length, but practically, generating words beyond 10-12 characters with full character sets creates impossibly large wordlists that exceed storage capacity.
Q2: How can I reduce the size of my wordlists?
A2: Use patterns (-t), limit character sets, use shorter password lengths, and compress output (-z).
Q3: Can crunch generate words in a specific order?
A3: Yes, crunch generates words in lexical order based on the character set provided.
Q4: How does crunch compare to other wordlist generators?
A4: Crunch is excellent for pattern-based generation and comes pre-installed on most penetration testing distributions. Alternatives like RSMangler or Mentalist offer different features like rule-based mutation.
Q5: Can I use crunch for non-English character sets?
A5: Yes, you can specify any characters in your custom character set, including non-English characters.
Q6: How do I handle crunch consuming too much memory?
A6: Use the -b option to split output into smaller files, or pipe output directly to other tools instead of saving to disk.
Q7: Is there a GUI version of crunch?
A7: While crunch is command-line only, tools like Mentalist provide GUI-based wordlist generation with similar capabilities.
Q8: Can I pause and resume wordlist generation?
A8: Yes, use the -s option to specify a starting point, and -e to specify an ending point.
Q9: How do I generate only unique words without duplicates?
A9: Crunch automatically generates unique combinations. For more complex deduplication, pipe output through sort and uniq commands.
Q10: What's the best way to use crunch for known password patterns?
A10: The -t option with placeholders is extremely valuable when you know or can guess part of a password structure, such as knowing that passwords start with a company name followed by numbers.
Conclusion: Mastering Crunch for Effective Security Testing
Crunch remains one of the most versatile and powerful wordlist generators available to cybersecurity professionals. Its ability to create targeted, pattern-based wordlists makes it invaluable for password testing, recovery operations, and security assessments, particularly when you have partial knowledge of password structures.
Whether you're a seasoned penetration tester or just starting in cybersecurity, mastering crunch will undoubtedly be a valuable addition to your skill set. By combining crunch with other tools like Hashcat, John the Ripper, and Hydra, you can create powerful security testing workflows that help identify and remediate vulnerabilities before malicious actors can exploit them.

Master Bettercap in minutes! Explore MITM attacks, ARP, DNS spoofing, Wi-Fi pentesting, and more wit…

Learn Wifite tutorial for Wi-Fi security auditing. Explore WiFi hacking concepts, WPS and WPA/WPA2 t…
Unlock the full potential of SQLMap for automated SQL injection testing. Learn to detect vulnerabili…