AI Just Made Password Cracking 100x Faster in 2025
Published on: August 23, 2025 |
Author: Bibek Singh
Introduction: Why AI Password Cracking in 2025 Is a Game Changer
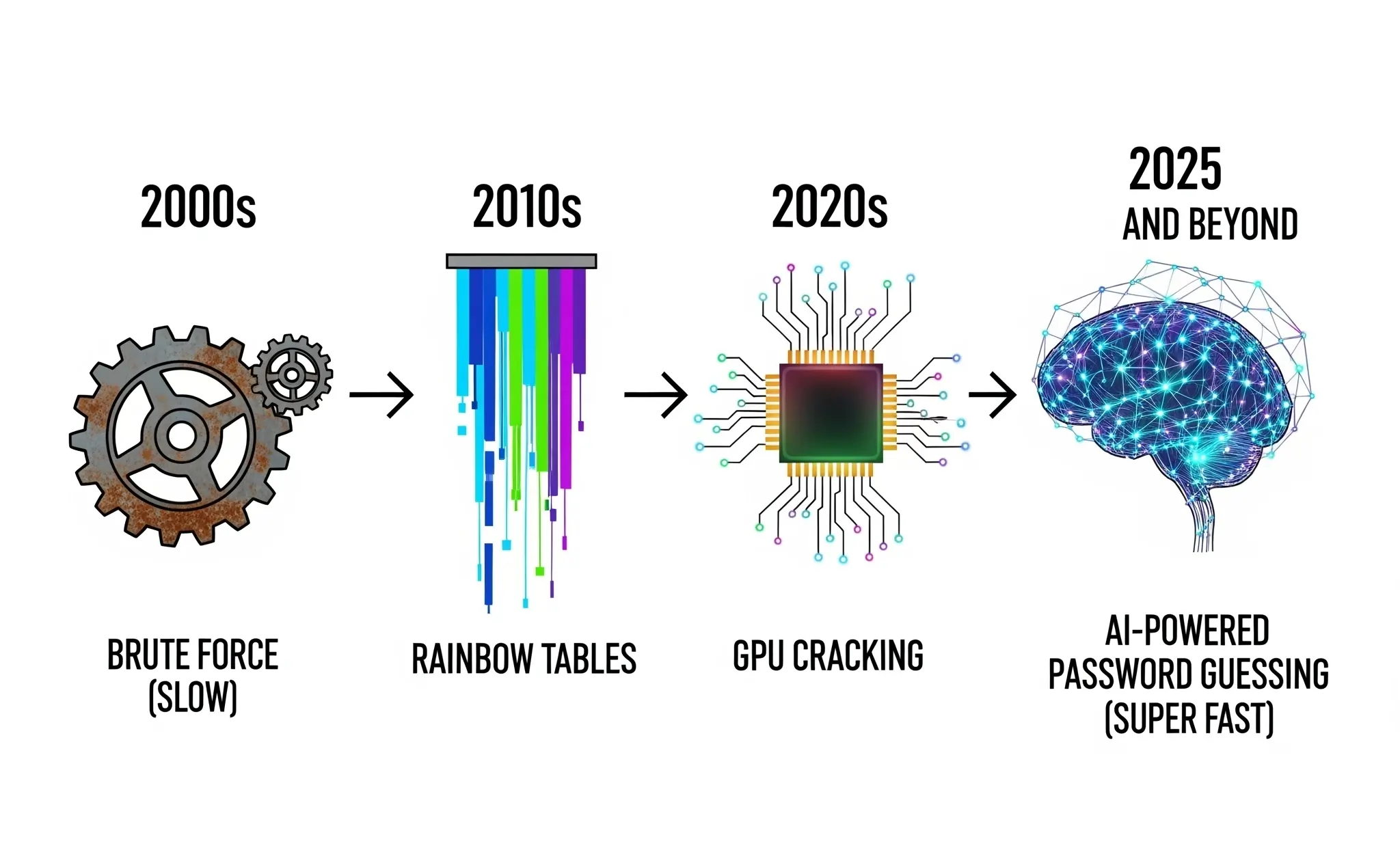
In 2025, AI-powered password cracking has completely changed cybersecurity. Previously, cracking passwords was slow and relied on either brute force (trying every combination) or using leaked password lists. Now, artificial intelligence, machine learning, and neural networks can predict passwords 100 times faster, making even moderately strong passwords vulnerable.
This has massive implications for anyone who uses digital accounts-whether email, banking, social media, or enterprise systems.
Searchers today are asking:
- How fast can AI crack passwords in 2025?
- What tools are used for AI password cracking?
- How can I protect my accounts from AI hackers?
This blog answers all these questions with detailed explanations, practical examples, and actionable solutions.
What Is AI Password Cracking and How Does It Work?
Password cracking is the process of recovering or guessing passwords to access protected accounts. Traditionally, hackers used:
- Brute Force Attacks: Testing every possible combination of letters, numbers, and symbols.
- Dictionary Attacks: Using lists of common passwords or leaked credentials.
- Rainbow Tables: Precomputed hash tables for faster password recovery.
These methods were often slow and resource-intensive.
AI-Powered Cracking in 2025
With AI, hackers now leverage:
- Neural Networks (e.g., PassGAN): These learn patterns from billions of leaked passwords and predict likely human passwords.
- Machine Learning Algorithms: These identify common substitutions like a → @ or o → 0 and human tendencies, like adding “123” or a year.
- GPU and Cloud Acceleration: Modern GPUs and cloud computing can test millions of guesses per second, making even strong passwords crackable in hours or days.
Why this matters: AI can now target human-like passwords, which are the most common. Instead of testing random gibberish, AI predicts passwords people are most likely to create, saving tremendous time.
Practical Python Demo: AI vs Brute Force
Here’s a safe, educational demo showing how AI-like guessing is faster than traditional brute force:
import itertools
# AI-like patterns learned from leaked passwords
ai_patterns = ["Password2025", "P@ssw0rd", "Qwerty123!", "LetMeIn!"]
target = "P@ssw0rd"
# AI prediction simulation
for guess in ai_patterns:
if guess == target:
print(f"[AI Found] Cracked: {guess}")
break
# Brute force simulation (very slow, only demo)
chars = "abc123P@sworD"
for length in range(1, 5):
for guess in itertools.product(chars, repeat=length):
if ''.join(guess) == target:
print(f"[Brute Force] Cracked: {''.join(guess)}")
break
- AI guesses are pattern-based, so it succeeds almost instantly.
- Brute force tries all combinations randomly and takes significantly longer.
This demonstrates why pattern-based AI cracking is so dangerous in 2025.
Why Your Passwords May Not Be Safe in today's era ?
Passwords once considered strong are now vulnerable. In 2020, a 10-character mix of letters, numbers, and symbols was sufficient. AI has changed that.
- 10-character passwords: Weak, easily broken by AI.
- 12–14 characters: Moderate safety, may resist casual attacks but not AI.
- 16+ characters: Strong, recommended for 2025.
Password Strength Estimator Example:
def crack_time(length, charset_size, guesses_per_sec):
total = charset_size ** length
return total / guesses_per_sec / (60*60*24*365) # years
brute_force_speed = 1e9 # guesses per second
ai_speed = brute_force_speed * 100
print("10-char password, charset=62")
print("Brute Force:", crack_time(10, 62, brute_force_speed), "years")
print("AI Cracking:", crack_time(10, 62, ai_speed), "years")
Explanation: Even a password that seems long could be cracked in hours or days by AI-powered methods.
Top AI Password Cracking Techniques
1. PassGAN: Neural networks predicting likely passwords based on leaked datasets.
2. GPU-Accelerated Brute Force: Modern GPUs (e.g., RTX 5090) massively increase guess speed.
3. Machine Learning Mangling Rules: Automatically applying substitutions and common patterns.
4. Hybrid Attacks: Combining AI prediction, dictionaries, and brute force for maximum speed.
These techniques make even complex passwords vulnerable if proper protection isn’t in place.
How to Protect Your Accounts Against AI Hackers ?
- 1. Use a Password Manager: Generates long, unique passwords for every login automatically. Avoid reusing passwords.
- 2. Enable Multi-Factor Authentication (MFA): Even if a password is compromised, MFA blocks unauthorized access.
- 3. Adopt Passkeys or Passwordless Logins: Modern authentication replaces passwords entirely with cryptographic keys stored on your devices.
- 4. Monitor Breaches Regularly: Check sites like Have I Been Pwned to know if your credentials are leaked.
Generate a Strong Random Password Example in Python:
import secrets, string
def strong_password(length=16):
chars = string.ascii_letters + string.digits + string.punctuation
return ''.join(secrets.choice(chars) for _ in range(length))
print("Strong Password:", strong_password())
Example Output: M!a9$z3L7x#Gq1@T
(Random, long, and secure against AI attacks)
Frequently Asked Questions:
Q1: How fast can AI crack a password in 2025?
- Weak passwords can be cracked in seconds to hours; stronger passwords (>16 characters) may take years.
Q2: Are 12-character passwords safe against AI?
- Only moderately. Passwords with 16+ random characters are recommended.
- PassGAN is an AI neural network that predicts passwords using leaked datasets, enabling much faster cracking.
Q4: How can I protect my accounts?
- Use password managers, enable MFA, adopt passkeys, and monitor breaches regularly.
AI-powered password cracking in 2025 is real and extremely fast. Short, reused, or weak passwords are vulnerable.
Protect yourself with:
- 16+ character random passwords
- Password managers
- Multi-factor authentication (MFA)
- Passkeys and passwordless logins
Note: Your security depends on acting before AI cracks your accounts.

Discover how hackers, apps, and websites track your exact location through your IP, GPS, and photos.…

Learn how to bypass firewalls for security testing. Step-by-step guide with Nmap, SSH tunneling, DNS…

Discover Cursor AI – the ultimate AI-powered code editor built on VS Code. Generate, debug, and opti…